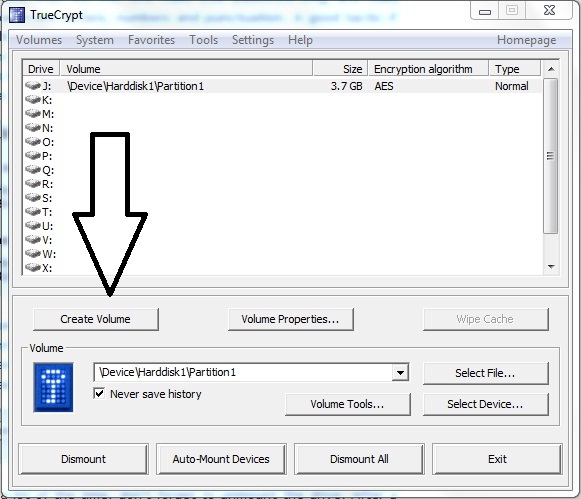
If your laptop, desktop, notebook or smart phone stolen, now don't worry for that. Now you can track your stolen PC or mobile phone free of charge, using "Prey".
If you set your devise status as "Stolen" in "Prey" web site control panel" then prey will collect following details and upload them to prey server.
- Network information. (remote and private IP addresses, gateway ip address etc)
- Picture of thief (If you configure your devise web came).
- Desktop screen shots.
- Total up-time.
- Logged user account name.
- Modified files details.
- Ruing programs.
- Active controls.
- WiFi information.
You can view that information on "Prey" web site control panel".
First of all you have to download and install "Prey" client in your devise, no matter its a portable devise or desktop PC.
Now "Prey" has windows, Linux, Mac and also Android OS clients. You can get that clients in here.
After you downloaded and install you "Prey" client you have to configure it.
Configure your Devise client.
- First step is setup reporting method.
After you double click Prey setup or start menu icon you can view following screen shot type window. Select its "setup reporting method".
- Setup how to view report.
- Create or log in your Prey account.
- Give your details.
That's all for configuring process.
Start tracking your stolen devise.
Note - If you devise stolen you have to immediately follow this process.
- Log in to your "Prey" account.
- Go to configuration.
- Set your devise status as "Stolen"
- Set how often you want generate your stolen devise report minimum time is 10 minutes.
- Select other settings as you want.
- Click "save".
Set prey as you normal windows start-up program.
You can set prey client as your normal startup program. To do that go to start menu and click prey client shortcut. Then select "Option for execution" like following screen shot.
Next window select "Run as window service" and also you can set reporting time in this window.
"Note"- Its better if you can hide this "Prey" shortcuts and also its installation folder. Prey normally hide its uninstaller icon in windows control panel.
Hide prey installed folder.
"Right click "Prey" folder and select "Properties". In"properties window" select its "general tab". Under general tab select hide and press OK.